In today’s digital age, cryptocurrencies have emerged as a revolutionary form of decentralized digital assets. As these assets grow in popularity and value, the need for secure storage mechanisms becomes paramount. Enter cryptocurrency wallets: digital tools designed to store and manage one’s cryptocurrency holdings. At the heart of these wallets are cryptographic keys—specifically, public and private keys—that play a pivotal role in ensuring the safety and accessibility of digital assets.
What is a Cryptocurrency Wallet?
A cryptocurrency wallet is akin to a digital bank account but for cryptocurrencies. It allows users to send, receive, and store their digital assets. Unlike traditional bank accounts, which rely on centralized institutions, cryptocurrency wallets operate in a decentralized environment, giving users full control over their funds.
Public and Private Keys: The Cornerstones of Security
Every cryptocurrency wallet is associated with two main cryptographic keys:
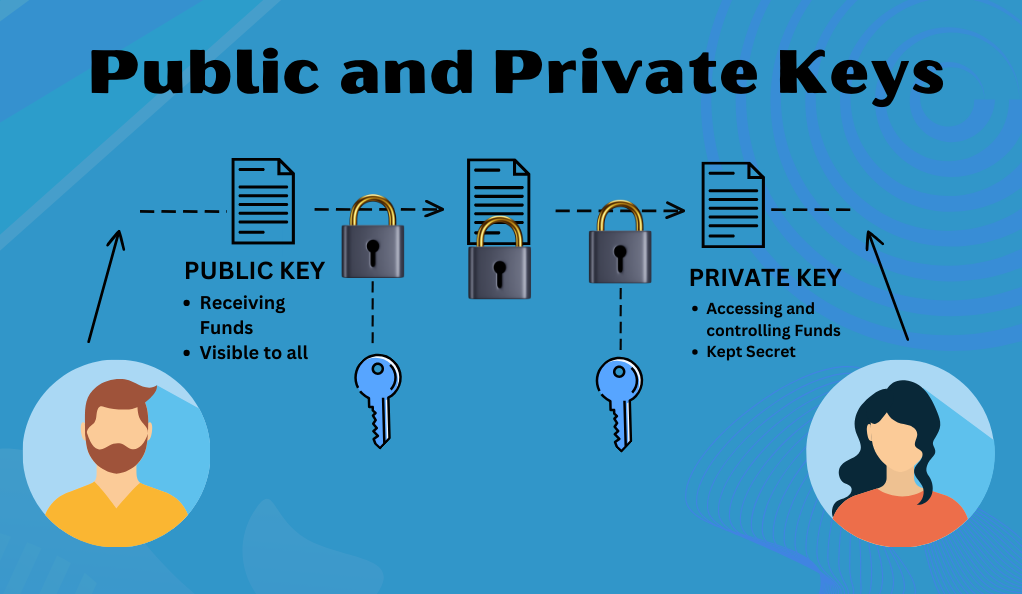
- Public Key: This is analogous to an account number. It’s what you share with others to receive funds. Anyone can see a public key, but it only allows them to deposit to the address associated with it.
- Private Key: Think of this as your password or PIN. It’s kept secret and is used to access and control the funds in the wallet. If someone gains access to your private key, they can control your funds, which underscores its importance.
The Imperative of Security
Given the decentralized nature of cryptocurrencies, the responsibility of safeguarding one’s assets falls squarely on the individual. There’s no bank or institution to fall back on in case of lost access or theft. This is where the significance of wallet backups and recovery phrases comes into play. They act as a safety net, ensuring that even if you lose access to your wallet—for instance, if your device is lost or compromised—you can still regain access to your funds.
The Basics of Cryptocurrency Wallets
Cryptocurrency wallets are more than just digital storage; they are sophisticated software programs designed to interact with various blockchain networks. They enable users to monitor their balance, send and receive digital currencies, and conduct other operations. Let’s delve deeper into the fundamental aspects of these wallets.
Types of Cryptocurrency Wallets
There are several types of cryptocurrency wallets, each offering different levels of security, convenience, and accessibility:
- Desktop Wallets: Installed on a personal computer or laptop, they offer a high level of security as they can only be accessed from the device on which they are installed. However, they can be vulnerable if the device gets infected by malware.
- Mobile Wallets: These are apps installed on smartphones, making them highly convenient for everyday transactions. They often come with added features like QR code scanning.
- Web Wallets: Accessed through browsers, web wallets are convenient but depend on third-party services, making them less secure than other wallet types.
- Hardware Wallets: These are physical devices, like USB drives, that store private keys offline. They are considered one of the most secure options since they are immune to online hacking attempts.
- Paper Wallets: As the name suggests, these are physical documents that contain both the public and private keys. They are generated offline and can be printed or written down.
Understanding Wallet Addresses
Every cryptocurrency wallet comes with a unique address, a string of alphanumeric characters. This address is derived from the public key and acts as the location where transactions are sent to and received from. It’s essential to understand that while wallet addresses are public and can be shared, the private key associated with that address must remain confidential.
Why Backups Matter
Imagine losing access to your wallet—whether through device failure, theft, or simply forgetting your access credentials. Without a backup, your funds could be lost forever. Backing up your wallet ensures that you have a way to recover your funds and access your wallet from a different device. It’s a safety measure that cannot be stressed enough, especially given the irreversible nature of cryptocurrency transactions.
Seed Phrases: The Backbone of Wallet Security
As we venture deeper into the realm of cryptocurrency security, one term frequently emerges as a beacon of hope for those fearing loss of access: the seed phrase. This seemingly simple set of words holds immense power in the world of digital assets.
Deciphering Seed Phrases
A seed phrase, often referred to as a mnemonic phrase or recovery phrase, is a series of words generated by a wallet, usually ranging from 12 to 24 words in length. This phrase acts as a master key to your wallet, allowing you to recover and restore your funds on any compatible device.
How Does It Work?
The seed phrase is derived from a random number, which then gets translated into a sequence of words from a predefined dictionary. This conversion from numbers to words makes it easier for users to note down and remember. When you input this phrase into a compatible wallet, it decodes the words back into the original number, which then regenerates your private key.
The Importance of Safekeeping
Given the power that a seed phrase holds, it’s paramount to keep it secure:
- Physical Security: Write down your seed phrase on a piece of paper and store it in a safe or a secure location. Avoid making digital copies that could be vulnerable to hacking.
- Confidentiality: Never share your seed phrase with anyone. Anyone with access to your seed phrase can access and control your funds.
- Redundancy: Consider making multiple copies and storing them in different secure locations. This ensures that even if one copy is lost or destroyed, you have backups available.
Restoring Access with Seed Phrases
Should you ever lose access to your wallet—maybe you lost your phone, your computer crashed, or you forgot your password—the seed phrase comes to the rescue. By entering the seed phrase into a new installation of your wallet software, you can restore your funds and transaction history. It’s like having a magic key to a treasure chest, ensuring that the treasure inside is never truly lost.
The Risks of Neglecting Backups
In the dynamic world of cryptocurrencies, where volatility is a given and the stakes are high, neglecting the importance of backups can have dire consequences. The decentralized nature of cryptocurrencies is both a boon and a bane. While it offers unparalleled freedom and control over one’s assets, it also places the onus of security squarely on the user.
The Perils of Overlooking Backups
- Irreversible Loss: Unlike traditional banking systems where forgotten passwords can be reset or lost funds can sometimes be retrieved, the cryptocurrency world offers no such safety net. If you lose access to your wallet and don’t have a backup, your funds are gone forever.
- Vulnerability to Theft: Without backups, if your primary device is compromised, you risk losing all your assets. A backup allows you to move your funds to a new, secure wallet before a malicious actor can.
- Device Failures: Electronic devices are not infallible. They can crash, get damaged, or become corrupted. Without a backup, a simple device malfunction could mean the end of your digital assets.
Real-World Consequences
There are countless stories of individuals who, due to a lack of backups, lost access to significant amounts of cryptocurrencies. Some misplaced their device, others forgot their passwords, and some were victims of theft or hacking. The common thread in all these tales is the absence of a backup, leading to irreversible loss.
Proactive Measures: More Than Just Backups
While backups are crucial, they are just one piece of the puzzle. Here are some additional measures to bolster your security:
- Regular Updates: Ensure your wallet software is always up-to-date. Developers frequently release security patches to address vulnerabilities.
- Two-Factor Authentication (2FA): Enable 2FA for an added layer of security. This requires a second form of verification, usually a code sent to your phone, in addition to your password.
- Cold Storage: Consider keeping most of your funds in cold storage, i.e., offline, and only a small amount in your ‘hot’ or online wallet for daily transactions.
Brainwallets: Memory-Based Security

In the vast landscape of cryptocurrency security, brainwallets emerge as a unique and intriguing concept. Unlike traditional wallets that rely on physical or digital backups, brainwallets depend solely on the power of human memory.
What is a Brainwallet?
A brainwallet refers to a cryptocurrency wallet that is created from a passphrase or a set of words memorized by the user. This passphrase is then converted into a private key, which can be used to access the associated cryptocurrency address and its funds. The idea is simple: if you can remember the passphrase, you can access your funds from anywhere, without the need for any physical or digital backup.
The Appeal of Brainwallets
Brainwallets offer a level of portability and freedom that is unparalleled. With no devices, no paper, and no digital files to worry about, your assets are accessible as long as you remember the passphrase. This memory-based security provides users with a sense of empowerment, as the safety of their assets lies in their own hands (or rather, minds).
Potential Pitfalls
However, brainwallets are not without challenges. The human memory is fallible. Over time, details can become fuzzy or even forgotten, especially under stress or with age. Additionally, if a passphrase is too simple or derived from common literature or music, it becomes vulnerable to brute force attacks. In such scenarios, hackers can employ powerful computers to try millions of word combinations in an attempt to crack the wallet.
Creating a Secure Brainwallet
If you’re considering using a brainwallet, here are some best practices:
- Complex Passphrase: Use a long and complex passphrase, ideally a random combination of words, numbers, and symbols.
- Regular Recollection: Periodically recall and use the passphrase to ensure it stays fresh in your memory.
- Avoid Common Phrases: Refrain from using quotes, song lyrics, or famous lines. These can be easily guessed.
Multisignature Wallets: Enhancing Security
In the quest for optimal cryptocurrency security, multisignature wallets stand out as a robust solution. These wallets, often referred to as “multisig” wallets, introduce an additional layer of authorization, making them a preferred choice for those seeking enhanced protection for their digital assets.
Understanding Multisignature Wallets
A multisignature wallet requires multiple private keys to authorize a cryptocurrency transaction. Instead of a single private key, which is standard for most wallets, a multisig wallet might require two, three, or even more keys before a transaction can be validated.
How Does It Work?
Imagine a safe deposit box that has multiple locks. To open it, you’d need several keys, each held by a different person. Similarly, in a 2-of-3 multisig wallet setup, you’d have three private keys, but only two would be required to authorize a transaction. This means even if one key is compromised, your funds remain secure unless the attacker gains access to the other required keys.
Benefits of Multisignature Wallets
- Enhanced Security: By distributing the authorization process across multiple keys, multisig wallets reduce the risk of funds being stolen due to a single compromised key.
- Collaborative Control: Ideal for businesses or groups where funds need joint oversight. No single individual can move the funds without the consent of the others.
- Backup Solutions: In scenarios where one key is lost, the remaining keys can still access the funds, ensuring that assets aren’t locked away due to a single lost key.
Potential Challenges
However, like all technologies, multisig wallets come with their own set of challenges. Their setup can be more intricate than standard wallets, potentially daunting for beginners. Coordinating transactions can become cumbersome, especially if multiple parties are involved and one or more are unavailable. Moreover, there’s the risk associated with losing multiple keys; if the number of accessible keys falls below the required threshold, the funds become permanently inaccessible.
Best Practices for Using Multisignature Wallets
For those considering multisig wallets, it’s essential to adopt certain best practices. Distributing keys among trusted individuals or entities is paramount, as is regularly testing the setup to ensure smooth operations. Staying informed about the latest in security practices and potential vulnerabilities can further bolster the safety of assets held in multisig wallets.
Best Practices for Wallet Security
As the world of cryptocurrencies continues to evolve, so does the landscape of threats and vulnerabilities. While innovations like multisignature wallets and brainwallets offer unique security solutions, it’s essential to remember the basics. Here, we’ll outline some best practices that every cryptocurrency holder should adopt to ensure the utmost protection of their digital wealth.
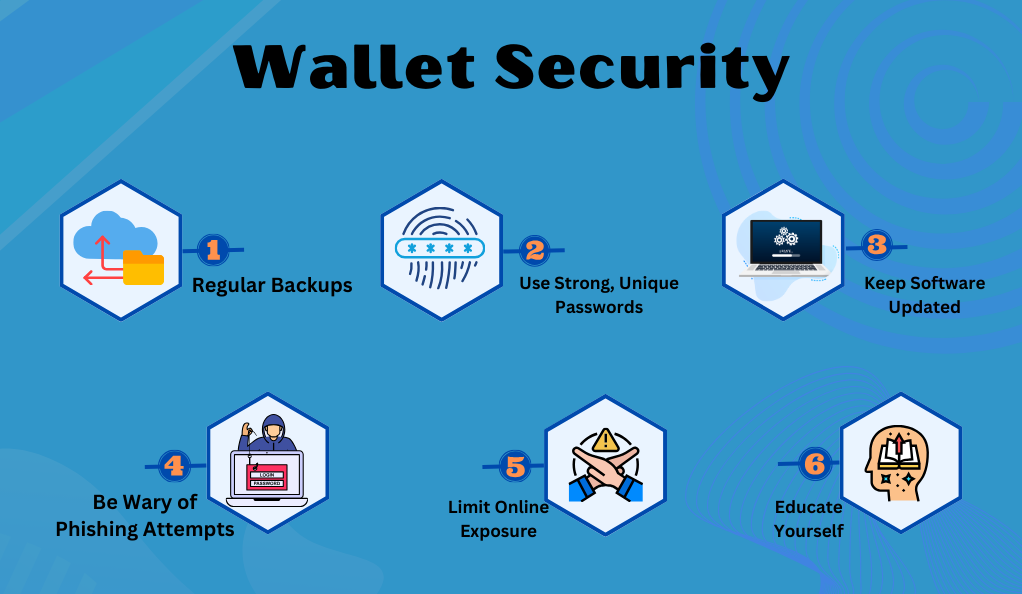
- Regular Backups
In the dynamic world of cryptocurrency, the importance of backing up your wallet cannot be overstated. Regular backups ensure that your digital assets are safeguarded against unforeseen events, such as device failures or accidental deletions. It’s not just about frequency; where and how you store these backups matter too. Storing backups in multiple locations, both digital and physical, ensures that even if one backup is compromised or destroyed, others remain intact, providing a safety net for your investments. - Use Strong, Unique Passwords
Passwords act as the first line of defense against unauthorized access. A strong and unique password, comprising a mix of letters, numbers, and symbols, can significantly reduce the risk of breaches. Given the complexity of such passwords, many users opt for password managers. These tools not only generate robust passwords but also store them securely, ensuring that your wallet remains protected from potential threats. - Keep Software Updated
The cryptocurrency landscape is ever-evolving, with new threats emerging regularly. To counter these threats, wallet software developers frequently release updates. These updates often contain security patches that address known vulnerabilities. By keeping your wallet software, as well as your computer’s operating system and other applications, updated, you ensure that you’re equipped with the latest defenses against potential security breaches. - Be Wary of Phishing Attempts
The digital realm is rife with phishing attempts, where malicious actors try to deceive users into providing sensitive information. Such attempts often come in the form of suspicious links or websites that mimic legitimate ones. It’s crucial to be vigilant. Always double-check URLs before entering any personal information and be skeptical of unsolicited emails or messages that prompt you to click on links or download attachments. - Limit Online Exposure
While online wallets offer convenience, they also expose your assets to potential online threats. For significant amounts of cryptocurrency, consider using offline storage solutions, such as hardware or paper wallets. These “cold storage” methods ensure that your assets remain offline, safe from online vulnerabilities. Additionally, when accessing your wallet or conducting transactions, avoid using public Wi-Fi networks, as they can be insecure and easily compromised. - Educate Yourself
Knowledge is power, especially in the world of cryptocurrency. Regularly educating yourself about the latest security threats and best practices can be your best defense against potential risks. Engaging with the cryptocurrency community, joining forums, or participating in discussions can provide valuable insights and timely warnings about emerging threats.
Conclusion
In the rapidly evolving world of cryptocurrencies, the decentralized nature offers both unparalleled opportunities and unique challenges. While this landscape empowers individuals with control over their wealth without intermediaries, it also places the responsibility of security squarely on their shoulders. From the basics of backups to advanced mechanisms like multisignature wallets, the tools for protection are vast. However, it’s our diligence, habits, and commitment to staying informed that truly safeguard our digital assets. As we navigate this digital frontier, let’s prioritize security, ensuring that our investments and endeavors remain protected and prosperous.





